Tajuk : MICROSOFT SPILLS THE BEANS: HERE’S WHY U.S. GOVERNMENT IS TO BLAME FOR “WANNACRY” CYBER ATTACKS
link : MICROSOFT SPILLS THE BEANS: HERE’S WHY U.S. GOVERNMENT IS TO BLAME FOR “WANNACRY” CYBER ATTACKS
MICROSOFT SPILLS THE BEANS: HERE’S WHY U.S. GOVERNMENT IS TO BLAME FOR “WANNACRY” CYBER ATTACKS
When you login on Monday for work, and your computer happens to be running on older versions Microsoft’s Windows such as Windows XP, chances are you could be staring at a screen screaming “pay me money to get your data back”. Call it blackmail, extortion or anything you like, but there’s no way you can get back your data without paying the ransom.
Many workers, particularly in Asia, had logged off Friday before the malicious software, stolen from the United States government, began proliferating and attacking around the world. The Friday’s cyber attack hit roughly 200,000 computers in at least 150 countries (according to Europol) around the globe. And the spread could be just the beginning.
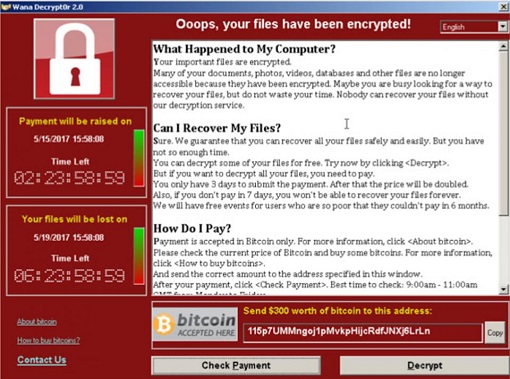
The virus, equipped with “a worm functionality” – called “WannaCry 2.0” – has already locked up computers in car factories, hospitals, shops and schools in several countries, including China and Russia. The virus encrypts a computer’s files and then demands a ransom – US$300 in Bitcoin – to recover their data, with no guarantee the computer would be released unharmed.
So far, nobody knows precisely who was behind the attack. Among the organizations hit were FedEx in the United States, the Spanish telecom giant Telefónica, the French automaker Renault, Nissan’s UK car plant, universities in China, Germany’s Deutsche Bahn federal railway system. The most disruptive attacks infected Britain’s National Health Service.
Russia, Ukraine and Taiwan had taken the heaviest casualties. Also known as “WannaCryptor 2.0” or simply “WCry 2.0”, the virus hits Russian Interior Ministry, Russian Railways and mobile service provider Megafon. In actuality, this is the second attempt at cyber-extortion. An earlier version, named WeCry, was discovered back in February this year.
The cyber attack was so disastrous that Microsoft has taken the rare step of issuing a fix for versions of Windows it had previously “retired” – the Windows XP, Windows 8 and Windows Server 2003. Support for Windows XP ended in 2014, 12 years after the software was introduced. But an estimated 7% of the world’s PCs still run on XP – that’s about 70,000,000 machines.
Microsoft, however, wasn’t impressed with the latest attack. And they’re blaming the U.S. government for stockpiling cyber weapons. How come? WannaCry uses vulnerability in old versions of Windows that was originally discovered and exploited by the U.S. National Security Agency as an offensive cyber-weapon. Everything remains secretive until hackers hacked the NSA.
A hacker group – known as Shadow Brokers – obtained an arsenal of cyber warfare tools in April from the NSA, of which the U.S. agency called “Eternal Blue”. But it wasn’t Shadow Brokers who were directly involved in the ransomware strike. Instead, some opportunist developers, who could be hackers themselves, spotted the leaks and added them to their own software and released them.
Microsoft President Brad Smith wrote on Sunday – “This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world.”
A 22-year-old British researcher who uses the Twitter name MalwareTech has been credited with “accidentally” helping to halt the spread of the assault. He noticed a bug in the virus – one of the web domains used by the attackers hadn’t been registered. So he registered the site, took control of the domain for US$10.69 and started seeing connections diverted from infected victims.
Unfortunately, the outbreak being stopped is only temporarily. The attackers will likely modify their code to remove the somewhat silly error or mistake, and restart their ransomware campaign. Already, new variants of the rapidly replicating worm were discovered on Sunday which did not include the so-called kill switch. An estimated US$30,000 in ransom has been paid by victims.
– http://ift.tt/1vPEu3w
.
✍ Sumber Pautan : ☕ Malaysia Chronicle
Kredit kepada pemilik laman asal dan sekira berminat untuk meneruskan bacaan sila klik link atau copy paste ke web server : http://ift.tt/2pDWQHW
(✿◠‿◠)✌ Mukah Pages : Pautan Viral Media Sensasi Tanpa Henti. Memuat-naik beraneka jenis artikel menarik setiap detik tanpa henti dari pelbagai sumber. Selamat membaca dan jangan lupa untuk 👍 Like & 💕 Share di media sosial anda!
When you login on Monday for work, and your computer happens to be running on older versions Microsoft’s Windows such as Windows XP, chances are you could be staring at a screen screaming “pay me money to get your data back”. Call it blackmail, extortion or anything you like, but there’s no way you can get back your data without paying the ransom.
Many workers, particularly in Asia, had logged off Friday before the malicious software, stolen from the United States government, began proliferating and attacking around the world. The Friday’s cyber attack hit roughly 200,000 computers in at least 150 countries (according to Europol) around the globe. And the spread could be just the beginning.
The virus, equipped with “a worm functionality” – called “WannaCry 2.0” – has already locked up computers in car factories, hospitals, shops and schools in several countries, including China and Russia. The virus encrypts a computer’s files and then demands a ransom – US$300 in Bitcoin – to recover their data, with no guarantee the computer would be released unharmed.
So far, nobody knows precisely who was behind the attack. Among the organizations hit were FedEx in the United States, the Spanish telecom giant Telefónica, the French automaker Renault, Nissan’s UK car plant, universities in China, Germany’s Deutsche Bahn federal railway system. The most disruptive attacks infected Britain’s National Health Service.
Russia, Ukraine and Taiwan had taken the heaviest casualties. Also known as “WannaCryptor 2.0” or simply “WCry 2.0”, the virus hits Russian Interior Ministry, Russian Railways and mobile service provider Megafon. In actuality, this is the second attempt at cyber-extortion. An earlier version, named WeCry, was discovered back in February this year.
The cyber attack was so disastrous that Microsoft has taken the rare step of issuing a fix for versions of Windows it had previously “retired” – the Windows XP, Windows 8 and Windows Server 2003. Support for Windows XP ended in 2014, 12 years after the software was introduced. But an estimated 7% of the world’s PCs still run on XP – that’s about 70,000,000 machines.
Microsoft, however, wasn’t impressed with the latest attack. And they’re blaming the U.S. government for stockpiling cyber weapons. How come? WannaCry uses vulnerability in old versions of Windows that was originally discovered and exploited by the U.S. National Security Agency as an offensive cyber-weapon. Everything remains secretive until hackers hacked the NSA.
A hacker group – known as Shadow Brokers – obtained an arsenal of cyber warfare tools in April from the NSA, of which the U.S. agency called “Eternal Blue”. But it wasn’t Shadow Brokers who were directly involved in the ransomware strike. Instead, some opportunist developers, who could be hackers themselves, spotted the leaks and added them to their own software and released them.
Microsoft President Brad Smith wrote on Sunday – “This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world.”
A 22-year-old British researcher who uses the Twitter name MalwareTech has been credited with “accidentally” helping to halt the spread of the assault. He noticed a bug in the virus – one of the web domains used by the attackers hadn’t been registered. So he registered the site, took control of the domain for US$10.69 and started seeing connections diverted from infected victims.
Unfortunately, the outbreak being stopped is only temporarily. The attackers will likely modify their code to remove the somewhat silly error or mistake, and restart their ransomware campaign. Already, new variants of the rapidly replicating worm were discovered on Sunday which did not include the so-called kill switch. An estimated US$30,000 in ransom has been paid by victims.
– http://ift.tt/1vPEu3w
.
✍ Sumber Pautan : ☕ Malaysia Chronicle
Kredit kepada pemilik laman asal dan sekira berminat untuk meneruskan bacaan sila klik link atau copy paste ke web server : http://ift.tt/2pDWQHW
(✿◠‿◠)✌ Mukah Pages : Pautan Viral Media Sensasi Tanpa Henti. Memuat-naik beraneka jenis artikel menarik setiap detik tanpa henti dari pelbagai sumber. Selamat membaca dan jangan lupa untuk 👍 Like & 💕 Share di media sosial anda!
dengan itu Perkara MICROSOFT SPILLS THE BEANS: HERE’S WHY U.S. GOVERNMENT IS TO BLAME FOR “WANNACRY” CYBER ATTACKS
Kini anda membaca artikel MICROSOFT SPILLS THE BEANS: HERE’S WHY U.S. GOVERNMENT IS TO BLAME FOR “WANNACRY” CYBER ATTACKS dengan alamat pautan https://timesnewmalaysia.blogspot.com/2017/05/microsoft-spills-beans-heres-why-us.html




0 Response to "MICROSOFT SPILLS THE BEANS: HERE’S WHY U.S. GOVERNMENT IS TO BLAME FOR “WANNACRY” CYBER ATTACKS"
Catat Ulasan